Example of phishing:
The phishing email looks like:

When you click the link it goes to the website looks like below
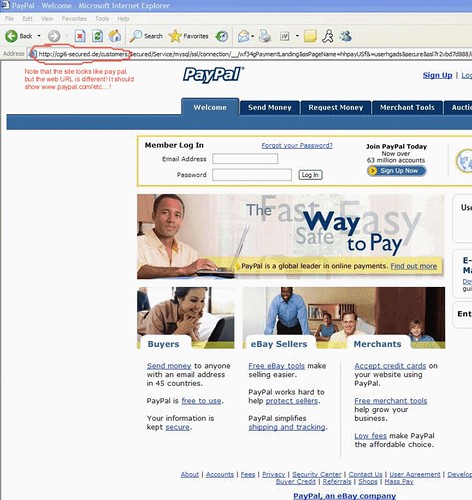
Phishing techniques:
Social engineering:
People have a built-in reaction to things that seem important. Subjects lines worded to arouse anxiety usually prompt immediate action. An email with the subject: "to restore access to your bank account ..." will usually get instant attention and prompt most people to click to read what happened.
There has been extensive research on the subject.
It is so pervasive that even corporate and government sites are actively informing their users on the issue.
Link manipulation:
Most methods of phishing use some form of technical deception designed to make a link in an e-mail (and the spoofed website it leads to) appear to belong to the spoofed organization. Misspelled URLs or the use of subdomains are common tricks used by phishers. In the following example URL, http://www.yourbank.example.com/, it appears as though the URL will take you to the example section of the yourbank website; actually this URL points to the "yourbank" (i.e. phishing) section of the example website. Another common trick is to make the anchor text for a link appear to be valid, when the link actually goes to the phishers' site. The following example link, http://infoguyz.blogspot.com/2009/03/about-internet-cookies.html, appears to take you to an article entitled "about-internet-cookies"; clicking on it will in fact take you to the article entitled "about RSS". In the lower left hand corner of most browsers you can preview and verify where the link is going to take you.
An old method of spoofing used links containing the '@' symbol, originally intended as a way to include a username and password (contrary to the standard). For example, the link http://www.google.com@members.tripod.com/ might deceive a casual observer into believing that it will open a page on www.google.com, whereas it actually directs the browser to a page on members.tripod.com, using a username of www.google.com: the page opens normally, regardless of the username supplied. Such URLs were disabled in Internet Explorer, while Mozilla Firefox and Opera present a warning message and give the option of continuing to the site or cancelling.
A further problem with URLs has been found in the handling of Internationalized domain names (IDN) in web browsers, that might allow visually identical web addresses to lead to different, possibly malicious, websites. Despite the publicity surrounding the flaw, known as IDN spoofing or homograph attack, phishers have taken advantage of a similar risk, using open URL redirectors on the websites of trusted organizations to disguise malicious URLs with a trusted domain.
Website forgery:
Once a victim visits the phishing website the deception is not over. Some phishing scams use JavaScript commands in order to alter the address bar. This is done either by placing a picture of a legitimate URL over the address bar, or by closing the original address bar and opening a new one with the legitimate URL.
An attacker can even use flaws in a trusted website's own scripts against the victim. These types of attacks (known as cross-site scripting) are particularly problematic, because they direct the user to sign in at their bank or service's own web page, where everything from the web address to the security certificates appears correct. In reality, the link to the website is crafted to carry out the attack, although it is very difficult to spot without specialist knowledge. Just such a flaw was used in 2006 against PayPal.
Phone phishing:
Not all phishing attacks require a fake website. Messages that claimed to be from a bank told users to dial a phone number regarding problems with their bank accounts. Once the phone number (owned by the phisher, and provided by a Voice over IP service) was dialed, prompts told users to enter their account numbers and PIN. Vishing (voice phishing) sometimes uses fake caller-ID data to give the appearance that calls come from a trusted organization
Damage caused by phishing: US$929 million(approx)
Anti phishing:
Social responses:
One strategy for combating phishing is to train people to recognize phishing attempts, and to deal with them. Education can be effective, especially where training provides direct feedback.One newer phishing tactic, which uses phishing e-mails targeted at a specific company, known as spear phishing, has been harnessed to train individuals at various locations, including United States Military Academy at West Point, NY. In a June 2004 experiment with spear phishing, 80% of 500 West Point cadets who were sent a fake e-mail were tricked into revealing personal information.People can take steps to avoid phishing attempts by slightly modifying their browsing habits. When contacted about an account needing to be "verified" (or any other topic used by phishers), it is a sensible precaution to contact the company from which the e-mail apparently originates to check that the e-mail is legitimate. Alternatively, the address that the individual knows is the company's genuine website can be typed into the address bar of the browser, rather than trusting any hyperlinks in the suspected phishing message.
Technical responses:
Anti-phishing measures have been implemented as features embedded in browsers, as extensions or toolbars for browsers, and as part of website login procedures. The following are some of the main approaches to the problem.
